So, it's come to my attention that malware writers that are attempting to get into, and onto a persons computer are not doing a good job of R&D Before they are writing their applications and are just making total idiots of themselves. In this blog post I'm going to attempt to cover something that should be discussed but never really is. How to write malware in the internet age and actually get your malware onto a target system.
Java Script
Most people know about javascript and how bad it is, and you should have no script and other tools to disable attackers from identifying your operating system. However, javascript is the first stop that we will discuss. And, we've enabled a little button to help explain what the code is doing. First we pass some code that will help us identify the operating system (later on we will show how it all comes together for an effective attack).
Figure 1.0 Javascript OS Detection
So we see a really simple approach to how this is done. If you've clicked the button "try it" you'd see that it comes back and says your operating system. In my case it was "Linux x86_64." This is cute, we have the operating system. But, what happens if we want to know if it's a specific operating system? Say we wrote malware to ONLY infect windows machines. How would we do this? Well, we would write some additional lines of code within the script and see what is returned. I'm going to do two scripts, and then a third that will help pull everything together.
Figure 1.1 Javascript to determine the OS and load it into a variable.
So now that we have this, lets get a bit picky and actually load this to where we can use it. In order to do this, use the following example:
Figure 1.2 Javascript to detect os and do something useful (Sloppy and long [keep it clean!]).
So now that we are building your scripts, we might want to demonstrate code that is looking for Linux, and windows. Here we are using the same example, BUT the main difference is each one is testing for the OS on the label. So, if it says "Linux." It's testing for Linux, and so fourth. Click each one and see what it says: | | |
From this example we can see that if we attack Linux or Unix you can get away with a shell script, or a POSIX C application. But, that might be too much work. Ideally for exploits, it's something completely different.
PHP Please
So in some cases you will have people that are running no script, and other tools that will limit and break the efforts of your javascripts. And, if you don't believe me I encourage you to download noscript for your browser and come back to this web location and try it. I bet you some of the page won't work / load and that the examples above will fail to produce anything good. So what can we do now? Well, we can push some of the detection mechanics over to the web / server side of the spectrum. And, in doing so it limits what the user can control. So, in order to do this we will first need a server that can support PHP.
The first stop we will make is to take a look at the PHP code that is being utilized. Below is an example of the code:
Figure 2.0 demonstrating the PHP syntax for OS Detection.
Now that we have this implemented, if we are running a server that supports PHP (considering our OS is Linux) the following is returned:
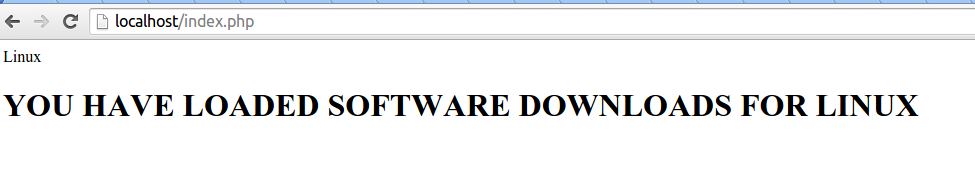
Displaying operating system
In order to do some fancy stuff, you can implement a page reload. In the next example the pages windows.html, linux.html and osx.html have been created on my local server. When this is done, we will detect the OS and pipe the user right to the page where they need to be. Of course you may need to do other things to make this come together, especially detection of javascript execution, etc. I will leave this to you in order to decide on how to do it. Now, once this is completed your code should be modified in order to look something like this:
Figure 2.1 PHP Syntax for loading an include file (Not done with security in mind).
Of course we see that the if statement and an include file has been added, we can do this for all the operating systems that are detected. This will load the right file and have you force the intended party to download a file for their specific operating system. When it all comes together the PHP script should look something like this:
Figure 2.1 PHP Syntax for loading an include file (Not done with security in mind).
Now that we've covered javascript and also explored PHP as a method to bypass the noscript issues that some of us may have, the next stop will be to visit the server-side technology ASP/X.
Flash
Flash is where the attackers will actually tie everything together. A cute little flash page will come up dressed up in the targets OS of choice (normally Windows) and start scanning to "identify" applications that you should remove that contain malicious code. The problem here is that there is no one size fits all, and most attackers don't realize this -- or, they are too stupid to code in the parameters to attack a plethora of operating systems. Which, if you ask me it's go big or go home.
The issue with Flash is that it also plays into the work aspect. Many of these attackers will target windows users because of the demographics. However, when the load the same tactic for all operating systems they kinda look stupid! Again, this deals with writing code as we have above to identify the operating system, then we have to write a flash application that looks like the operating system that we are targeting, and of course different versions of malware. C / C++, should it be POSIX? or do we write each for the specific os that we've detected and load which we feel is right. Maybe VB, and C? Who knows?!
I do realize that this document can be mistaken for a document that can be utilized to assist the attackers in attacking the internet user. Or, the not so tech / security savvy. Like I tell students in the introduction and advanced class, there are things you can do to protect yourself. It may range from what you currently have to expensive hardware / software to do the job. Below I'll try to get you a few key details on what you can do in order to protect yourself and what it may mean when you are surfing the internet.
Keep Your Syphilis to Yourself -- Thanks!
With some firewalls, and or content protection appliances (software, hardware, or a combination of) you can specify where you want to load flash content from. This type of filtration goes on the grounds that you know you will be visiting youtube.com, and maybe other flash based web sites and that's it. Then, if you venture outside of your comfort zone you can enable or add this to your protections appliance.
Another method that you can provide for yourself (and if you're a home user there is a bit of a learning curve) is to purchase a firewall like sonicwall or even WatchGuard. With certain settings (HTTP Proxy) you can actually filter out content types you don't want to download, and of course enable a set listing of applications that should be omitted, and to the extent which domains you will be downloading from. For instance, microsoft.com, apple.com, and other web sites that are "trusted." You simply allow those domains to server up .exe, .sh, .com, .dmg files and any other locations that try to "force" this type of download will be denied.
For users who have Google Chrome, you can download and install an application such as "FlashControl" You can cop the link by click on Flash Control and you will be taken directly to the web location. for FireFox users, you may want to download Flash Control for Firefox at the link provided, or Click Here. Again this will depend on content settings, and what you've white listed. It will also stop applications from auto-loading so you don't get the crap scared out of you in the middle of the night when you hear voices talking and you're home alone without mental problems.
Regarding the javascript issues, you will need to set a white list for the javascripts, and or web pages utilizing something called noscript. You can download that in the firefox extensions directory. Considering we will not cover how to set this up, it will be based on your preferences. For the chrome users you can check this link out here: ScriptBlock for Google Chrome
