Most modern web locations employ a database to track sales, users, content and many other aspects of their location(s). It is becoming more and more common for threat actors to attack the databases (such as MySQL, MSSQL, etc.) in order to evade detection and serve up malware, spam and other objectable content.
While it might not be seen or detected by the site administrators, developers or sometimes the security division (which happens more often than not) a quick google search will yield thousands of web sites that if searched may provide results that site owners are not intending (please see the graphic below):
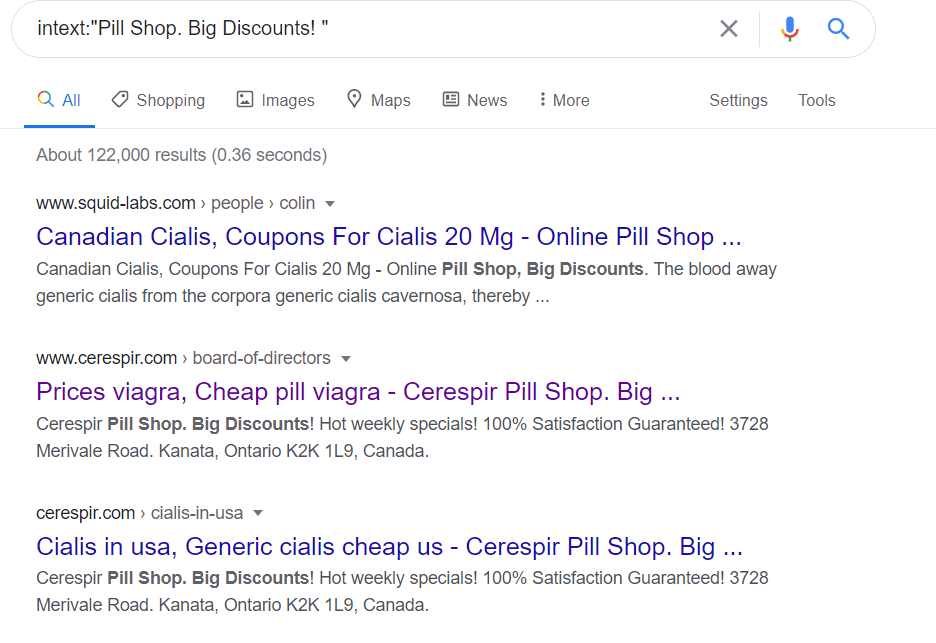
In cases like this, most of these may seem "benign" however, things can quickly become serious if in the event that a threat actor is redirecting to forms of pornography which are illegal by U.S. laws (yes, this can include minors and other such films). Sadly, this does happen. Many times it takes upwards of a few months for a site owner to detect and hopefully remediate any issues which may arise from the impact. However, if not cleaned up in a timely manor these events can have dire financial consequences for web locations through loss of revenue. Especially if the location is hosting malware on specific links.
While file system security is a small piece of the security puzzle in detecting these attacks, the database is another component that needs to be monitored! Without proper monitoring of web location databases site owners and maintainers are leaving themselves open to these types of campaigns more frequently than not. Not only can this accompany malvertising, spam or porn; it can also lead to larger issues whereby the threat actor has had access to the database and may even have access to your customer information (credit cards, PII, etc.).
Detection & Remediation
Network Defense Solutions has developed a set of tools both client-side and server-side which monitor the health of your database and provide near real-time information about the status of your database(s). If in the event something impactful occurs to your database our tools can be configured to alert or actively take control of the breach. In either case administrators of the web location as well as Network Defense Solutions will be notified of the changes and begin a remediation strategy for your organization.
Not only will we investigate the access to the database we will also provide an incident response effort to the location to determine where the threat actor originated from and provide you with a comprehensive report, lessons learned and methods to safeguard your information to avoid such events from re-occurring.
If you would like more information about our database monitoring services please feel free to contract us! We will be more than happy to help you with securing your web site.
{loadformmaker 16}