Introduction
The purpose of this article is to help security professionals in training to develop their skills using john the ripper, jtr or simply: john. The tool is a Linux password cracker that can check for password matches by comparing a password list, hashing that word and looking at the hash that has been loaded into it.
This document will be broken down by some of the tools and utilities that accompany john and, which can be found on the john the ripper github: John the ripper - github. This document WILL NOT cover the installation, setup or configuration of other packages which depend on John.
Please note that considering all the utilities work the same, we've only covered 3 of the utilities as the commands are similar.
The Testing Process
So because of previous instructing experience, I will need to state that password cracking can take some time. YOU WILL NOT be able to crack passwords like you see on NCIS or any other TV shows. It just doesn't work that way unless you work for the government and have access to the faster cracking setups. But, that is a conversation for another day. With that out of the way, you are limited by a few things. 1) The amount of time you want to exhaust or have to live, 2) the amount of processing power you have available (C/GPU) and, 3) the size of your password file. Yes, in this case size does matter!
This document assumes (please don't make an ass of u and me) you already have a dumped file with a hash ready for the crackin' if not, don't worry. I'm sure the document that referred you to this document pointed out how to do it. However, for brevity we will also show you how to do this for the selection you are making. We might even ask you a few questions before we set ya up ;-)
Understanding The Tools
For the tool selection, we are basically doing an ls on the entire directory of john. If something made it's way into this listing in error, we'll filter it out when we get there. There are A LOT OF TOOLS in this section for john. So, CTRL+F and have your way with the materials.
Cracking the Files
The exports for your cracking pleasure can come from a few sources. The primary source is during an attack or some type of exposure. Think a share or, AWS bucket that is exposed that may contain these types of files. Lastly, you might be doing some form of forensics where you may need to crack encryption in order to prosecute.
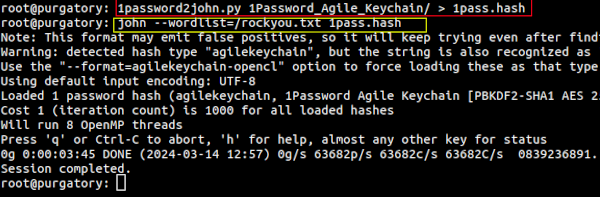
1password2john 1Password_Agile_Keychain/ > 1pass.hash
Understanding the command: 1password2john is one of the applications used to extract the hashes we want to crack. The 1Password_Agile_Keychain is the directory where the full. The > is a redirect for the output where we will be storing the hashes we want to crack. In this case, 1pass.hash
In this case, since we have already redirected the output we will now use john in order to crack the has with any of our password files. Here, we are using the rockyou password file.
Now that we have a hash we want to crack, we issue the command:
john --wordlist=/rockyou.txt 1pass.hash
this will then attempt to or, crack the main password for the 1pass file(s) that we've obtained.
Understanding the command: we are using john because we want to invoke a crack session using --wordfile=/rockyou.txt a word file located in the root of your drive. Next we specify 1pass.hash which is the file that we dumped the credentials to. The program will run for a while until a hash has been detected.
If all comes together quite well we should see something like this:
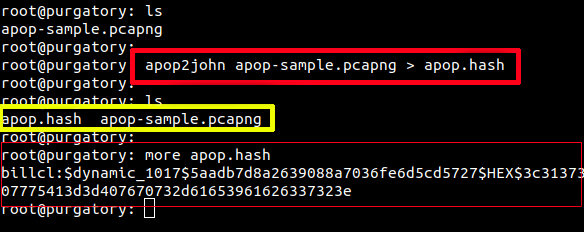
apop2john apop-sample.pcapng > apop.hash
Understanding the command: the apop2john command is called to start extraction from the apop-sample.pcapng file. Lastly, we are redirecting the output to apop.hash as this will be the file that we will be cracking. A sample of this output can be seen below:
Now that we have extracted the password hash, we can crack it with john (note that we are not specifiying the encryption type as it is already included). The command we will be using is as follows:
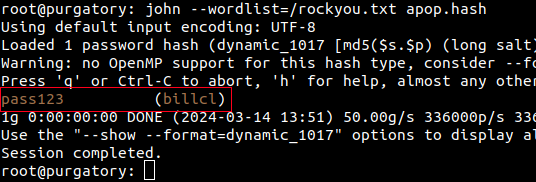
john --wordfile=/rockyou.txt apop.hash
Understanding the command: we are using john because we want to invoke a crack session using --wordfile=/rockyou.txt a word file located in the root of your drive. Next we specify apop.hash which is the file that we dumped the credentials to. The program will run for a while until a hash has been detected.
If the password is cracked, we should see something like this:
Command: bit2coin2john wallet* > bitcoin.hash
Understanding the command: We will launch the bitcoin2john command and issue the command against any of the wallet* files and finally we will redirect the output to a bitcoin.hash The next set of commands we will issue will be to crack the password from a password list. See the image below for the commands we've issued:
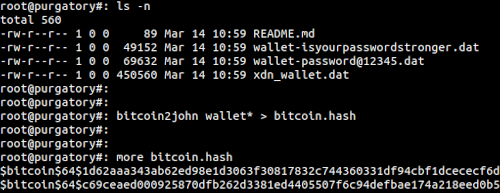
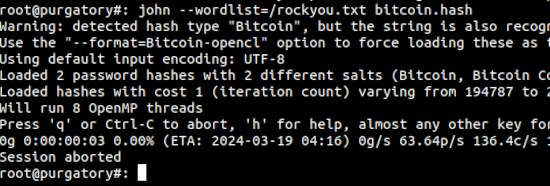
Command: john --wordlist=/rockyou.txt bitcoin.hash
Understanding the command: We run john with a --wordlist= option pointing to our wordlist of /rockyou.txt. From here, we also point john to the bitcoin.hash file where we've dumped the hashes from the wallets that we've discovered.