A set of tools to assist your small business identify malware risks, phishing and training to better prepare your organization to respond to an attack. Our tools allow you to handle identification of threats as well as arm your staff with the tools they need in order to identify, contain, respond and categorize attacks before they become an issue. Network Defense Solutions, Inc. also provides managed solutions to keep malicious content off your network and test it in a secure and sound location.
- Malware Analysis
- Phishing Analysis
- Hybrid Analysis
- Malware Analysis Training
- Phishing Analysis Training
- Malware & Phishing Analysis Training
- Managed Analysis
- Unmanaged Analysis
- Sample Report
- Request a Quote
Malware Analysis
In 2017 malware had cost small - medium sized businesses $2.2 Million U.S.D. Fast forward to today, in 2019 the average cost is approximately $3 Million dollars. From ransomeware alone the average 6 day cost to a business is $54,904.00. With malware attacks on the rise the cost in 2020 and beyond will only go up in value and the number of incidents will increase. Is your small - medium sized business prepared for such an event? In most cases smaller organizations are not. This can be include many reasons, of the top cited: The cost of security tools and, services.
Understanding the malware that is attempting to enter your network has a few major advantages. 1) Understanding the major attack venues threat actors are attempting to exploit can better prepare you for an incident. Are you receiveing mostly crypto-driven malware? Are they exploits targeting specific applications? Or, are they trojans which can either allow access to third parties or exfiltrate information to competitors? 2) Understanding the attack can better prepare you for how to respond to it. crypt-driven malware requires a strong backup / backup policy. Trojans will rely on your firewall policies, what ports are needed for work and which ports are not. Exploit driven attacks will help you understand what applications are being targeted, their update schedule, firewalling and what information is at risk. 4) Lastly understanding where these applications communicate allow you to draw a better picture of where your attackers may be based and what blocking strategy will work best for your business.
From VBA/VBS to binary files and batch scripts we have the expertise to de-obfuscate code, understand what it's doing within the environment, obtain the traffic between the remote hosts it is communicating with and in some cases provide code samples your team can further scrutinize. Most tools on the market only go as far as to determine what a given piece of malware is doing and what to block, not to mention the monthly costs! Other commercial tools cost thousands and only provide IOC details to block.
With custom static and dynamic tools that help your team dive into your threat actors arsenal you can also arm your team with the necessary toolkit to understand how to better defend your network. With guided software and scripts (Linux, OSX / macOS, Windows) your entry-level analysts can provide meaning full reports on a level that seasoned analysts would create. This not only saves you time, it also saves you money! With managed tools provided by Network Defense Solutions, Inc. your toolkit will always be kept up-to-date. Especially with the tools that we write, maintain and develop.
Phishing Analysis
Phishing attacks are the one attack which attempts to side-step your security controls and, attack the weakest link within the security landscape. Your employees. The associated costs of phishing are as follows:
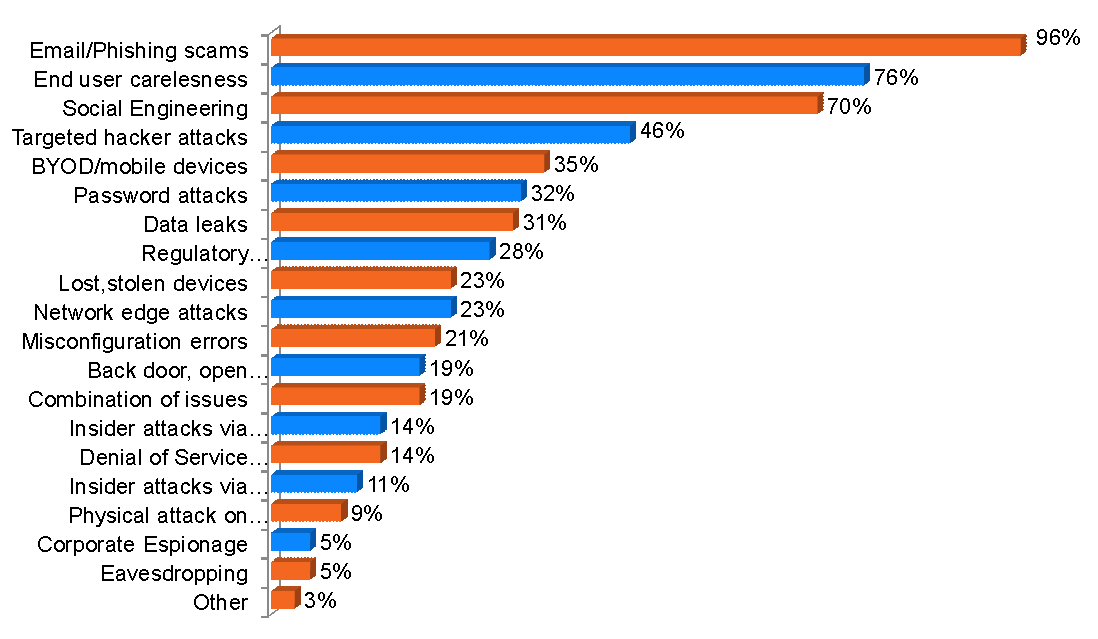
While malware does make up a significant portion of the attacks / attempted attacks a component of infection is related to phishing. With phishing attempting to appear as though it is coming from a legitimate location (and many times the fakes are just as convincing as the real thing) it is far too often that an employees credentials are obtained, which in turn can create additional security issues for your environment and your intellectual property.
Network Defense Solutions, Inc. has created a new vetting process for phishing that will assist your organization with identification and classification of these types of attacks. From E-mail analysis to Domain analysis and blocking, our tools assist with every step of the process making it easier for your company and, employees to spot and report phishing attacks.
Our tools encompass e-mail headers and e-mail tracking, domain activity and tracking, campaign identification and how the campaign works. The tools we've created also go as far as to obtain advancd IOC's when available and dissection of those IOC's.
Collection of phishing IOC's can assist your organization in applying filters to your web location(s) in order to quickly detect malicious files before they become a problem for you. Phishing campaigns on a vulnerable site can lead to Google ranking issues as well as risk score indexes which can further damage your online reputation.
Hybrid Analysis
Our hybrid analysis provides you tools that will enable you to easily create your own reports, scan for malicious files and phishing campaigns as well as provide details on how to use the information gained to better protect your organization. This approach can be implemented within house or as a monthly service where you can submit your samples and links and have one of our trained professionals analyze the samples and provide meaningful feedback.
Each malware report will contain detailed static analysis information and dynamic information after a sample is executed and run in our safe environment. After each analysis our environment is then reset and the next analysis is started. No analysis will be run with a previously tained environment.
The Hybrid Analysis provided by, Network Defense Solutions, Inc. encompasses tools and scripts that we have created as well as the human eye in order to make sense of all the information that is within the samples you send. The hybrid analysis reports will also include static analysis, dynamic analysis, domain analysis, e-mail header analysis and other details that are provided to us at the time.
Malware Analysis Training
Our malware analysis training will teach your security team how to analyze malware as a static binary (Mac, Windows, Linux) as well provide dynamic analysit which will examine traffic and disassembly with Olly, GDB and, IDA. Students will learn to write their own python, batch and bash scripts to utilize along with their analysis as well as which tools to utilize during a system triage.
Students will learn how to obtain IOC's, utilize online resources to further track those IOC's and how to implement blocks regarding the IOC's they have found. Students will also learn how to implement their own contained environments and build out their own labs. The course will also teach students how malware may also detect lab environments and what they can do to combat these checks as well as report creation.
The course will also cover setting up a minimal network for capture, and also introducing techniques to confuse new malware which checks the system for "use." Students will then be given live malware samples to analyze (over 200 samples) and tasked with creating their own reports. The class can be delivered in person for a week at a time, or online at the same pace. Extensions can be provided to meet certain criteria for our customers and students.
In addition to static and dynamic analysis and tool creation students will also learn to de-obfuscate VBS/PHP/JAVA malware that is sent to your organization so other teams (intel or threat hunting) can review the code and provide more meaningful feedback and protection.
Phishing Analysis Training
The phishing analysis course is a two day course that will cover topics from reading e-mail headers, researching the source of a message, contents of an e-mail as well as domain analysis and finally IOC collection.
Students will learn how to read e-mail headers and pull information from the header that can be utilized in source discovery. Reading domain outputs to determine additional information about their advisary, researching the company the threat actor is supposedly from and finally interrogation of the phishing campaign itself.
Advanced interrogation techniques will teach students how to obtain the phishing campaign for off-line analysis, tracking potential developers of the campaign and if the campaign has been seen / leaked online. Additional searches will help students to identify the social media accounts of the threat actors as well.
The course will also cover source code review of the campaign as well as reversing any obfuscated code.
Malware & Phishing Analysis Training
Our malware and phishing analysis course encompasses both forms of our class into one. Students are given materials for both segments of the classes as well as video examples and an online forum where they can ask questions and engage with their peers. This course is designed to encompass both sets of attacks that organizations like yours face on a daily basis. Students will learn how to spot phishing tests throughout an organization as well as review files for potential malware.
Segments of this course can also be delivered to non-technical employees regarding the handling and review of potential malicious content so it does not affect your environment. These courses can be set up as an on-going training throughout the year or for a select group. This training consists of 1 week of hands-on labs, report and tool creation as well as utilizing the tools available to the student (Linux, Windows, OSX)
Managed Analysis
Managed analysis are a set of tools (5 virtual machines in total) that will allow you to test both malware and phishing. The tools provided will have a 360º view of threats that affect Linux, Windows and MacOS. These tools tools and virtual machines ARE NOT licensed copies. Each customer / environment is responsible for their own licensing. The managed tools allow your environment to set how the labs will interact with the internet, what update schedule you will use, and what ranges of IP addressing are utilized within your environment.
The lab environments are only supported via e-mail and are not maintined by Network Defense Solutions, Inc. Once the sale has been made customers will receive a hard drive in the mail with instructions for setup. Shipping takes 2 - 5 business days. A list of services that are being utilized will also accompany the lab documentation so that if in the event you need to set your own security protocols for the labs you can do so.
Managed analysis is only provided for VMWare. No other formats are supported at this time as our labs run off of ESXi. We also encourage you to do the same on a different subnet from your own environment. Managed environments are responsible for their own report creation and IOC collection.
Unmanaged Analysis
Unmanaged analysis provides you with a location where you can connect, upload and detonate any malware samples you choose. Additionally you can also opt-in for an advanced service where samples are sent directly to us and we analyze them and provide the reporting for you.
Unmanaged analysis removes the headache of storage space, maintenance, network setup and the risk of destroying your own environment. Our segments can be accessed via SSH, RDP and, TeamViewer. Once within the lab you can choose which operating system you would like to provide your analysis against and start in that area first.
You will have access to a number of tools for IOC collection, dynamic analysis and triage of events. If you opt-in for the advanced unmanaged package you will receive assistance in report creation to present to other security teams.
Sample Reports
Cost is a big concern after an attack. Without a backup strategy or a method to respond to an attack 90% of businesses that are not prepared will fold within the year they come back online. Having a security suite, and a scanning methodology will assure this does not happen to you! You can easily export and explore the information, logs and artifacts that were part of the breach, identify objects that you would normally skip over and create a robust report. Not only will you get to see what files were created, but how and where your information was accessed and from what location(s). Having an overall 360º of protection will provide you with a birds eye view of the attack.
Not only can you identify how the attack was executed against you, you can even determine if any of your backups were affected by the incident. This will help you pull a known good configuration of your web site to re-deploy, or even better -- allow you to determine which databases and files were unscathed in the attack. Not only will this save you precious time, it will also save you on costs associated with the cleanup.
