Launching a log analysis after or before a breach shouldn't have to be an all day affair. Network Defense Solutions, Inc. Has developed new tools that will help you collect artifacts, block IP addresses and assist with filing out abuse reports that you can send to your Host, and the offending IP ISP. With built-in scanners for malware, malicious users, CnC domains, malicious IP addresses, spam e-mail addresses our suite of tools would be THE ONLY tool you would need in order to scan, detect and block web application attacks.
File Integrity
File integrity scanning is an important part of the web application protection suite. The software maintains each file, permissions and their respective hash. If a file has been deleted, modified or created the software can either actively take control of the issue, or simply report it. These scanners and tools can help you identify new threats, archive suspected files along with location, and MD5 and assist in determining what type of file you have (given you have these features setup and installed).
With an easy to use interface, the integrity scanner can break down Modified, Deleted and Created along with options you can use to create a report. With reporting, you can also scan documents for errors, and information leakage that may be utilized in future attacks against your systems. Should an issue arise -- you can tell the software to put up a temporary unavailable page / under construction while a backup is pushed to the remote location*.
Web Log Analysis
Web Log Analysis Tool - Screen Shots
Features
| Feature Set | ||
|---|---|---|
| Supports IIS | Supports Apache | Support Nginx |
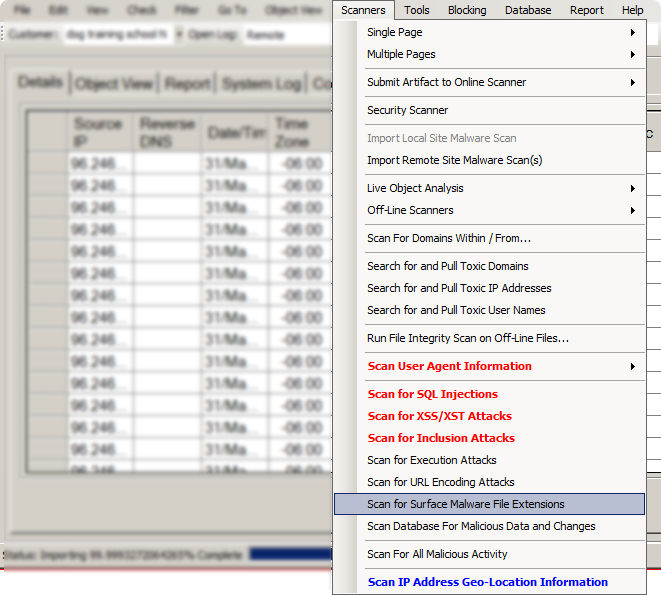
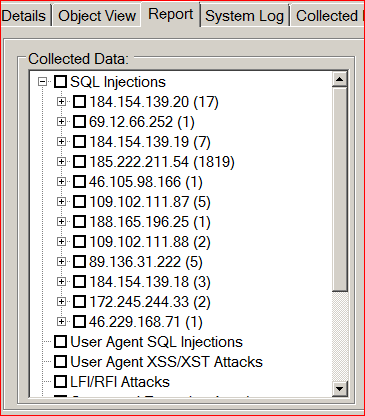
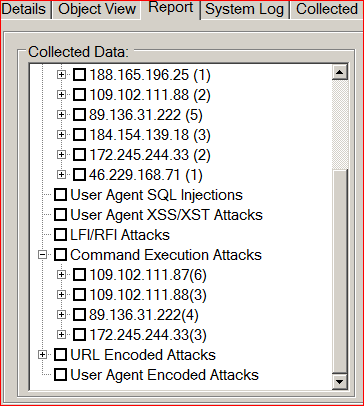
| SQL Attack Detection | Diractory Traversal, LFI/RFI | XSS/XST Attack Detection |
| Command Execution Detection | Shared Hosting Malware Scan Removal | VPS Hosting Malware Scan Removal |
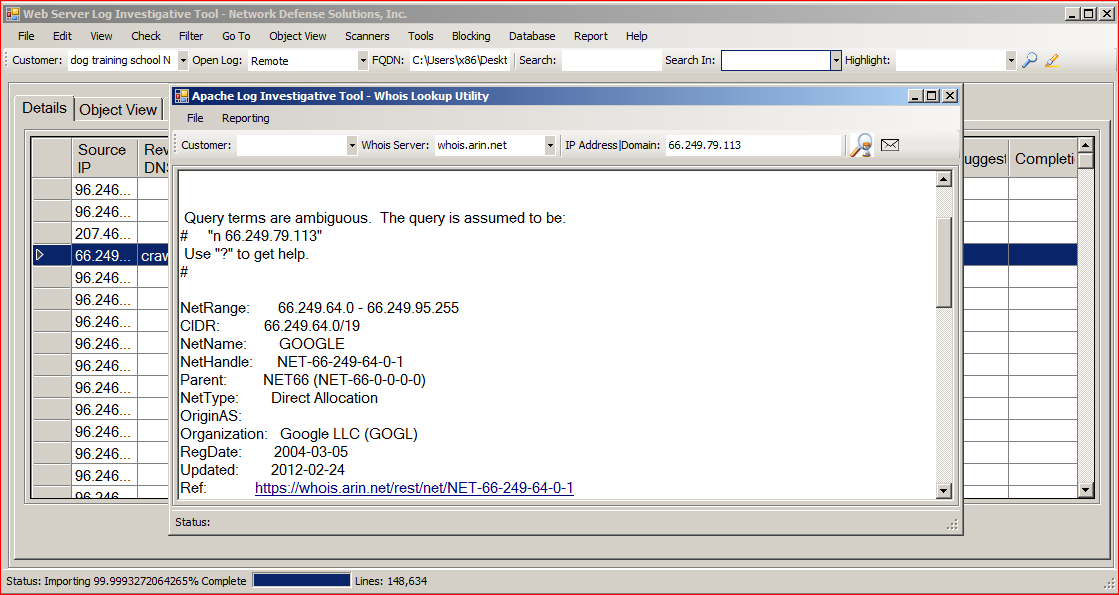
| Reverse DNS Lookup | Whois (Reverse, IP, Referrer) | IP Address Physical Location Lookup |
| Show Data/Time in Local Time Zone | Filter your IP from Database | Block by IP, Referrer or crawler |
| Block by .htaccess | Block by generatning Cisco rule | Block by generating iptables rule |
| Scan pages for iframes and other potentially unsafe code | Search backup for malware | Scan for Toxic Users |
| Scan for Toxic Domains | Scan for Toxic IP Addresses | Automatically Pull Logs After Defacement* |
| Run file Integrity scan | Scan User Agent for Malicious Activity | Block Low,Medium or High threats or block all 3. |
| Add recommendations, suggestions and take action against issues. | Create reports for client, abuse dept. and host. | France |
| Download, scan and forensically archive objects of interest. | Create, modify or remove database scan patterns, malicious CnC or other archived information to match your needs | Write reports based on collected data. |
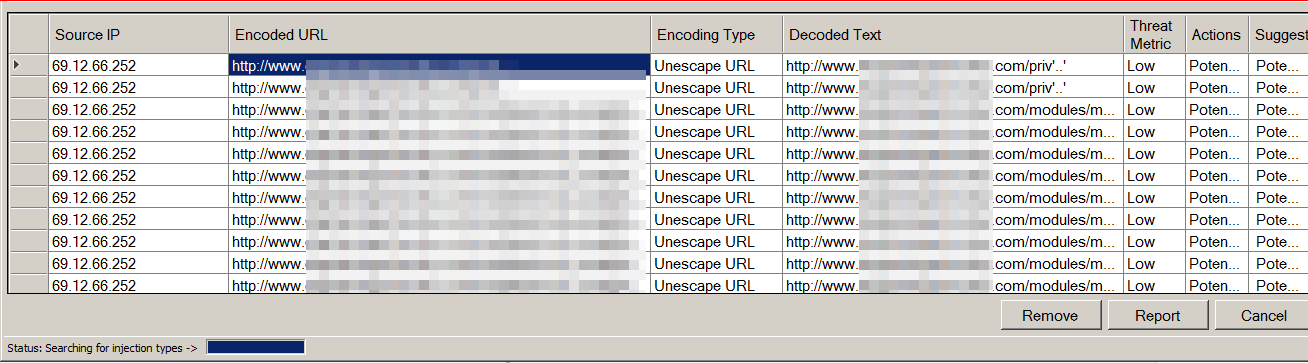
| Integration with other scripts/tools by Network Defense Solutions, Inc. | Standard / Advanced Filtration Menu for finding and sorting information | URL Decoders from Base64 and other escape sequences to human readable (with depth list) |
...AND MANY MORE FEATURES...
Analysis of large logs can take days or weeks after an attack has been successfully launched against a web server. Whether you're running Apache or Nginx, our software cam import the logs and sort them based on relevant information. You can scan attacks (XSS/XST, LFI/RFI, Encoding, SQL Injection, Directory Traversal, etc) locate malicious IP addresses, group events and label them low, medium, high -- find out about reverse DNS, whois and geographic location. Our tools can even break down the attacks by IP address and display them in time chronological order. If that's not enough, you can even export the attacks, sort them by time and replay them to see exactly what the attacker had obtained!
Within this tool, if you are on shared hosting, or VPS hosting, you can export: .htaccess rules, iptables rules or cisco rules for blocking IP addresses that may be causing your web location issues. Baked into the software is a database scanner along with a myriad of other tools to help you investigate and respond to issues.
Multiple Levels of Access Control
Discovered an attacker coming from an IP address, or network range? Our tools allow you to block via multiple methods. PHP, .htaccess, Cisco Switch/Router, iptables so no matter what your setup consists of you have a script that is created that you can copy and past into the console you are using to assure that you're being protected.
Cost Reduction
Maintaining a business presence online doesn't always stop at marketing, and web development. Many organizations DO NOT have a security solution or BCDR policy in place that can protect them if in the event of a breach or, defacement. To further complicate the situation costs can easily start at $25,000 a year. Not to mention support of the products and any other bolt-on services that a corporation may sell you.
Our log analysis software and attack detection tools are designed to be affordable and allow you to dedicate your own team, or our team to your needs. With 24/7 Monitoring you can set our tools to do the job for you with alerts, or have a person review the information in order to keep you safe. Therefore reducing costs and helping you save!
If you are looking for more information regarding our log analysis tools, please feel free to request a quote below. A representative will be glad to reach out to you and discuss what options you have available and what would work best for your small business!